Breach Fatalism Is Dead: The Identity Layer War Begins
When Fortresses Fall to the Gatekeepers
In an age where digital walls are tall but not always wise, cybersecurity is finally moving past the era of breach fatalism—that fatalistic shoulder shrug that declared breaches inevitable no matter the fortress. Attackers, once mythologized as battering rams, have grown charming, sidestepping defenses through the identity layer—the very systems meant to keep them out.
Recent breaches at high-profile companies shed a harsh spotlight on this irony. The perimeter has become quaint, and defenders now face a new reality: identity is both the playground for attackers and the frontline for defenders.
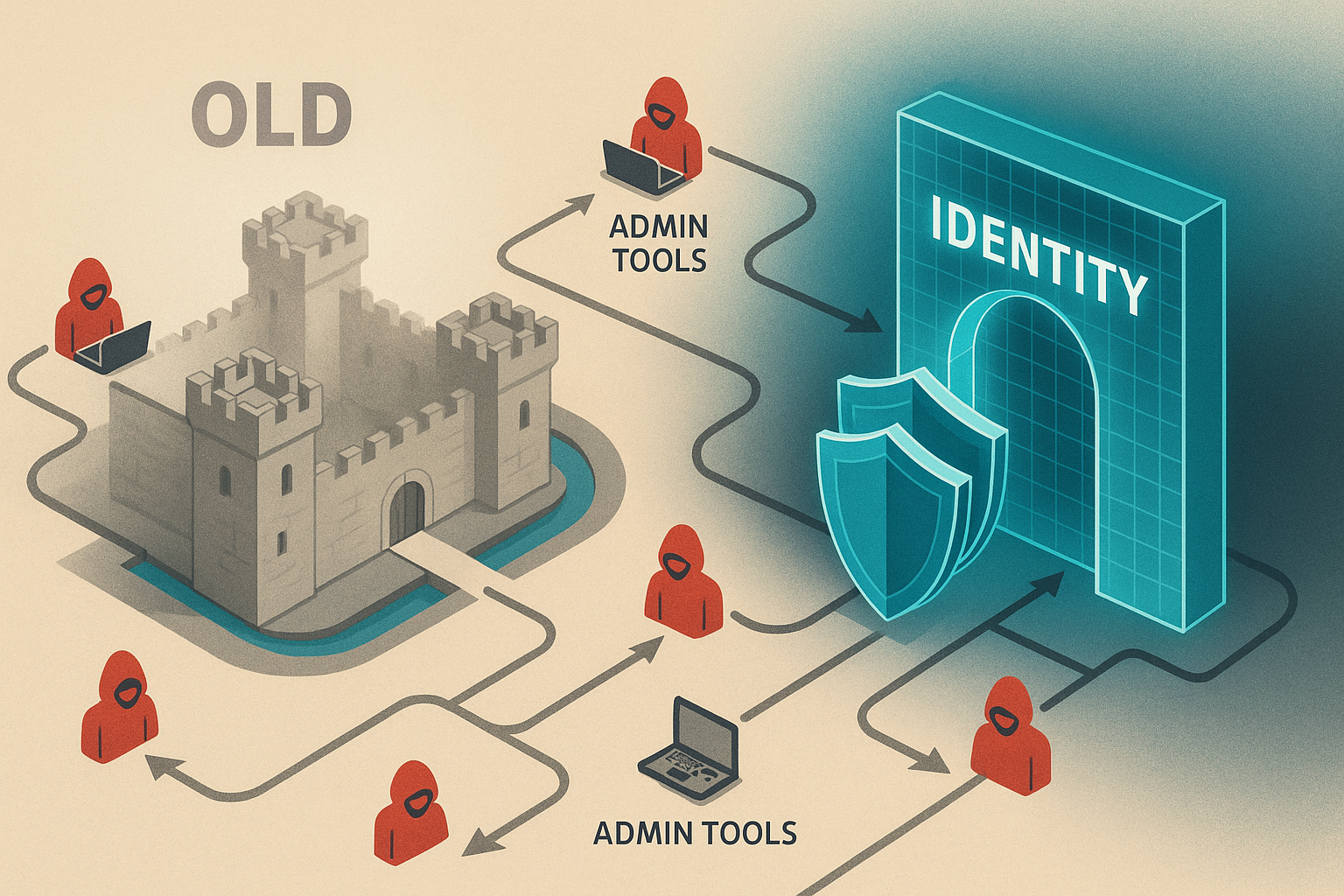
The End of “Set It and Forget It” Security
Once upon a time, defenders built digital castles with moats of multi-factor authentication and watchtowers of complex passwords. But like the mythic Trojan Horse rolled past dozing guards, attackers today simply talk their way in. The rise of credential phishing, MFA fatigue attacks, and session hijacking exposes deep flaws in legacy authentication systems—each band-aid solution now just another hurdle for hackers to leap with disturbing grace.
The Anatomy of Modern Breaches
Case studies abound: Caesars Entertainment, MGM Resorts, and Cisco all fell prey to attackers who charmed credentials from employees or battered support systems. MFA, once the golden child of security checklists, became a weakness when bombarded by push requests. These incidents show a new order—hackers no longer break in; they’re invited, or at least convincingly self-invited, through the front door.
Identity as the Battlefield
The traditional security perimeter—firewalls, antivirus, and intrusion detectors—has become Swiss cheese. Now, the identity layer, the digital equivalent of the castle steward, is the weak link for defenders and the prime target for attackers. The mission is evolving: defenders must move from merely detecting breaches after they happen to preemptively shutting down would-be intruders at the gate.
The Regulatory Squeeze
With data protection laws like the EU’s GDPR wielding heavy fines, the cost of carelessness rises. The message is clear: treating identity as an afterthought is no longer tolerated. Compliance mandates are nudging organizations to invest in advanced defenses—think behavioral analytics, zero-trust models, and AI-powered anomaly detection working long shifts at the gate.
Attackers Go Native: Living Off the Land and the Patchwork Problem
Hackers have also grown resourceful. No longer do they haul in bespoke malware—84% of serious breaches now abuse legitimate tools like PowerShell or netsh.exe. These everyday utilities, administrators’ best friends, moonlight as attackers’ multipurpose gadgets. Detecting the line between routine use and digital malfeasance now requires not just vigilance, but nuanced, continuous surveillance.
Meanwhile, relentless patching of software vulnerabilities plays out like a frantic game of whack-a-mole. From Fortinet’s buffer overflow bugs to SAP NetWeaver loopholes, vulnerabilities keep vendors and infosec teams on their toes, often outpaced by attackers ready to exploit the next unfinished patch cycle.
Law Enforcement’s Tightening Grip—And the Evolving Threat
Regulators and law enforcement aren’t sitting idle. The high-profile extradition of data bazaar operators and ongoing crackdowns on cybercriminal marketplaces show a growing global resolve. Yet, for every marketplace shuttered, threat actors evolve, inventing new ways to funnel stolen identities and escalate the arms race.
From Breach Fatalism to Breach Prevention: A New Playbook
The lessons are clear: the era of “deploy and forget” security is over. Proactive identity threat prevention—with AI-driven monitoring, zero-trust architectures, and shrewd user education—is now the expectation, not the exception. Training employees to spot phishing and repeated MFA requests is necessary, but without shoring up the core identity systems, it’s like locking the door while leaving the windows wide open.
Cyber defenses must embrace complexity and adapt, always one step ahead of attackers wielding familiar tools in unfamiliar ways. The real battle isn’t just technical; it’s a design flaw decades in the making—a call to treat identity as an ongoing siege, not a box to tick.
Conclusion: The Siege at the Gate
As cybersecurity pivots from defeatism to proactive defense, the irony remains thick: years spent erecting barriers, only to see attackers stroll in under friendly guise. The perimeter is outdated—the new war is at the identity gate. Organizations must now ask: Are we prepared for identity warfare, or waiting for the hackers to send the dinner invitations?