When Cybersecurity Breaches Make Panic Buttons Fashionable
Rethinking Digital Defenses in the Hot Seat
In an era where innovation sprints and lurking cyber threats jog serenely beside, one can’t help but wonder: why aren’t corporate boardrooms kitted out with emergency panic buttons yet? The latest wave of breaches, from legacy telecoms to financial giants, is a forceful reminder that no digital fortress is truly impenetrable.
Cellcom’s recent multi-day service blackout and the simultaneous siege on Australia’s largest pension funds demonstrate how swiftly cyberattacks can unravel even the best-laid security plans. Let’s unravel how these breaches unfolded—and just how fragile our connected reality might be.
Case Study: Cellcom Under Siege
The Anatomy of a Telecom Takedown
Cellcom, a telecommunications player with well over a century in the business, recently fell victim to a cyberattack that disabled parts of its network for five days. Despite the company’s seasoned defenses, attackers managed to disrupt isolated sections crucial to service delivery. Notably, Cellcom’s rapid response—including swift engagement of external cybersecurity experts and notification of the FBI—prevented any clear breach of customer data.
Yet, this incident proved that even significant investments in security offer no ironclad guarantee. The imperative for ever-evolving contingency planning grows only starker in the wake of such sophisticated assaults.
Pension Panic Down Under
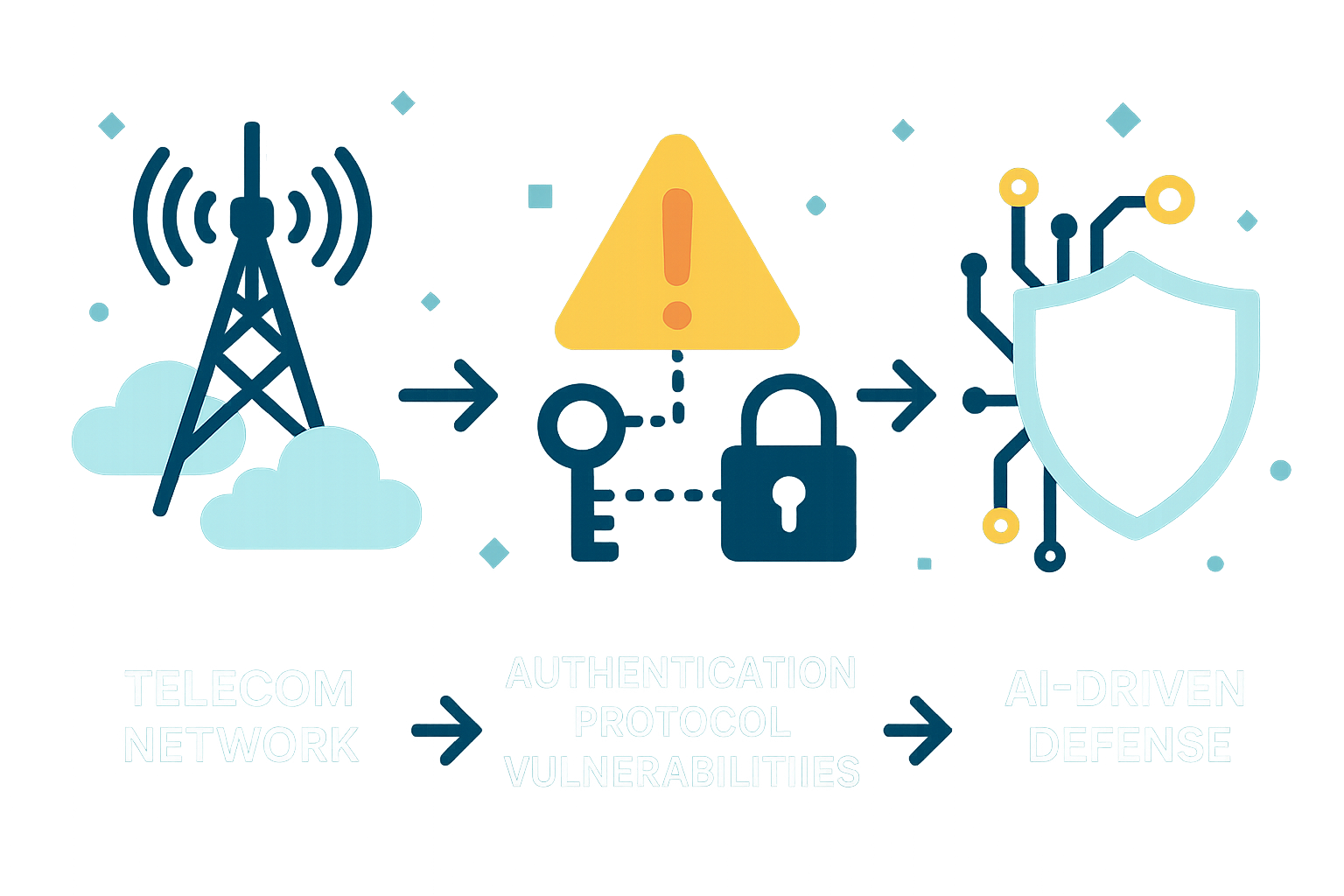
Cracks in the Armor: Credential Exploitation
Meanwhile, across the globe, coordinated attacks on Australia’s largest pension funds exposed vulnerabilities that were hiding in plain sight: authentication protocols and weak credential management. Cybercriminals wielding stolen credentials sidestepped security using common, easily bypassed measures like SMS-based two-factor authentication, compromising over 20,000 accounts and absconding with nearly half a million Australian dollars.
This saga is an unambiguous call for stronger authentication methods and ongoing adaptation as attackers innovate—and as financial systems become ever more interconnected and inimical to complacency.
Cybersecurity’s New Battleground: Progress and Pitfalls
The AI Dilemma
These attacks are just the tip of an iceberg submerged in a turbulent sea of change. According to the 2025 Thales Data Threat Report, breach numbers may be down, but anxiety about phishing, credential compromise, and evolving threats remains evergreen. Layered atop that is the rapid expansion of AI in high-stakes industries like finance and healthcare—a double-edged sword if ever there was one.
AI brings the promise of sharper detection and faster incident response. Yet, it also introduces novel points of failure, with many organizations racing to secure their AI systems in real time. The consequences of an overreliance on nascent, sometimes opaque, AI models raise practical and ethical specters that are still far from exorcised.
Balancing Innovation Against Insecurity
The rush to digitize, automate, and optimize is inevitable, but so are the risks that accompany such ambition. Organizations stand at a crossroads: fortify defenses and cultivate a pervasive culture of cybersecurity awareness—or await the day their fridge, TV, or smart assistant lobs a ransom note their way.
Perhaps it is time for cybersecurity best practices to find a place in kindergarten curricula. Until then, vigilance, flexibility, and a pinch of irony may be our best safeguards against tomorrow’s digital storms.