Adidas Breach Reveals Hidden Dangers of Third-Party Trust
When the Weakest Link Isn’t You: The Adidas Cyber Saga
In the high-stakes theater of cybersecurity, even titans can trip over their own digital shoelaces. Adidas, the global sportswear colossus, has landed in the headlines—not for its latest sneaker drop, but for a sobering breach via a third-party service provider.
This saga isn’t just a headline-grabber; it’s a stark case study in the perils of modern cyber dependencies. As supply chains stretch and interlink, companies increasingly trust outsiders to handle critical customer data—often at their own peril. Welcome to the era where the chain is only as strong as its least careful vendor.
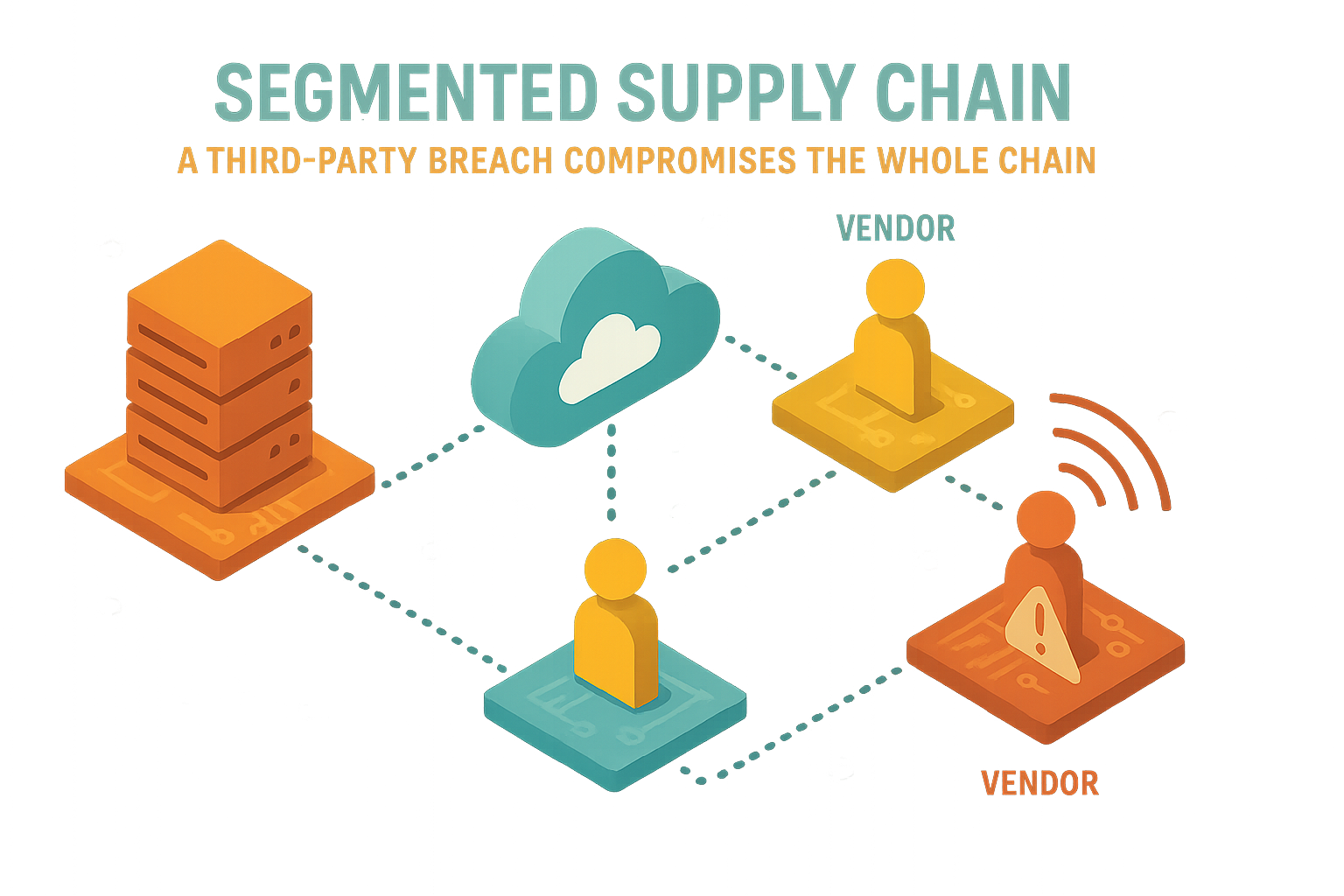
The Third-Party Trap: An Industry-Wide Paradox
Adidas’s woes perfectly illustrate a mounting irony: outsourcing, once touted as an operational boon, has become a cyber risk multiplier. The breach, which involved unauthorized access to customer contact data through a vendor-run help desk, didn’t expose passwords or credit cards. Still, even “innocent” data points can be a cybercriminal’s golden ticket for phishing and social engineering attacks.
Data Is Data—And Cybercriminals Love It All
Contact info may seem pedestrian next to credit card numbers, but to modern threat actors, it’s prime bait. This breach underlines how seemingly trivial details can unlock downstream havoc—proof that no data, however “surface-level,” should be written off as harmless.
The Breach in Context: An Epidemic of Vendor Vulnerabilities
The Adidas incident is not an outlier; nearly a third of breaches in the latest Verizon Data Breach Investigations Report stem from third-party vendors—a number that’s doubled in two years. With similar incidents erupting across South Korea and Türkiye, it’s clear: this is not Adidas’s headache alone, but a systemic threat woven through global supply chains.
The digital domino effect is in full swing. Each new integration, cloud service, and contractor multiplies a company’s cyber exposure. Unfortunately, the bad guys know this far better than most C-suites care to admit.
The Regulatory and Geopolitical Headwinds
Businesses face a double bind: regulators demand ever-stricter data protection just as adversaries sharpen their digital knives. Compliance fatigue sets in because sprawling vendor ecosystems are notoriously hard to police—especially as AI and automation crank up both attack speed and complexity.
Hybrid Cloud: Both Solution and Achilles’ Heel
The pivot to hybrid cloud architectures promises flexibility, but also broadens the threat landscape. The Adidas breach is a timely reminder: cloud convenience comes with an implicit invitation for sophisticated, AI-enabled attackers—unless every vendor is kept on a tight cyber leash.
The Marketing Irony: Trust, Undone by Trusted Partners
Here’s the kicker for marketing leaders: those hard-won customer relationships, forged with clever personalization tools, are now only as resilient as the supply chain’s weakest cybersecurity “apex.” Brands that trumpet innovation and trust risk having it all unravel via a partner’s slip-up—a modern ouroboros if ever there was one.
What Now? Beyond PR Band-Aids
For Adidas (and everyone else), this isn’t just another PR crisis—it’s a wake-up call. The quaint assumption that perimeter defenses suffice is dead. Today, security must saturate every contract, every handshake, every API call. Automation and relentless vendor scrutiny are now non-negotiables, regardless of the exhaustion or expense.
If a global juggernaut like Adidas can falter, midsize and emerging companies must not be lulled into complacency. The future belongs to those who treat zero trust not as a buzzword but as a baseline survival instinct.
The Uncomfortable Truth and the Way Forward
In this interconnected digital marathon, vulnerabilities multiply in the most unexpected places—frequently outside your direct control. The irony is biting: business thrives on collaboration, yet security demands skepticism bordering on the paranoid.
So, as we lace up for the next lap, perhaps it’s time to start vetting not only our vendors, but their vendors as well. Or maybe—just maybe—it’s time to let algorithms handle privacy training while we plot ways to stay one digital step ahead.
In the end, the Adidas breach reminds us: in the game of cybersecurity, it’s rarely the user, but always the chain. And that’s a reality every brand must face before the next breach knocks at the door.