184 Million Accounts Compromised: The Infostealer Data Breach Debacle
When “Unprecedented” Becomes Routine: A Breach for the Record Books
Yet another week, yet another data breach—only this time, the stakes include nearly every digital identity you hold dear. In the latest digital heist, over 184 million login credentials stretching from Facebook to iCloud were laid bare, courtesy of a vast trove of unencrypted files, ripe for the picking.
With credentials spanning banking, health platforms, and government portals, this isn’t just a privacy nightmare; it’s a front-row ticket to the cybercrime Olympics. Brace yourself: the wild west of the web just got wilder.
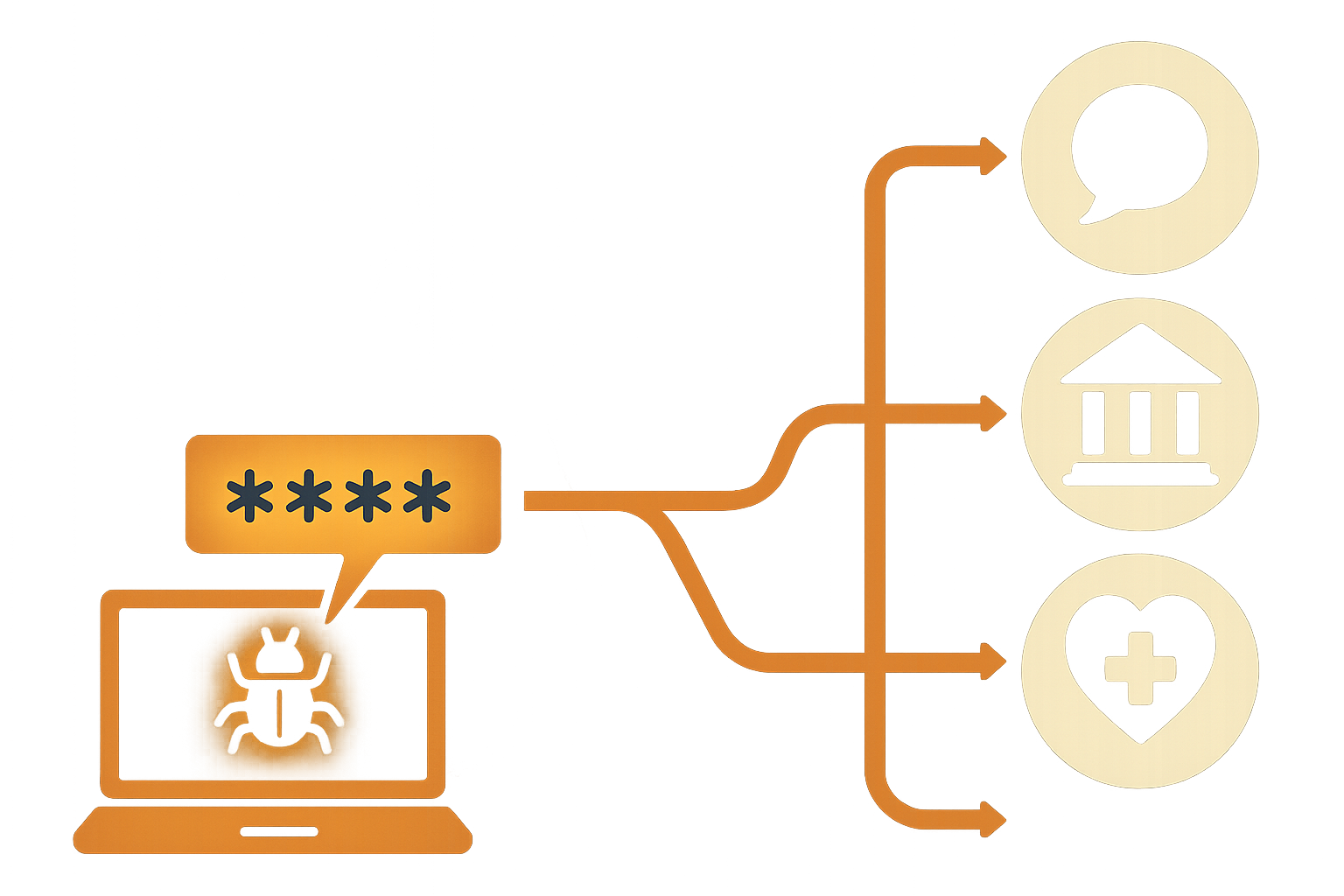
The Anatomy of a Mega Breach
Infostealer Malware: From Browsers to Crypto Wallets
Security researcher Jeremiah Fowler uncovered a 47.42 GB database packed with login details—left accessible on the open web like a picnic for hackers. The culprit? Infostealer malware, the Swiss Army knife of cyberespionage. This malicious code swipes everything from saved login credentials to crypto wallet keys, tossing in screenshots and keystroke logs for good measure.
Operating from behind cloaked domains and masked registrations, the orchestrators of this breach have retreated into anonymity. Though access to the exposed database has now been shuttered, even Houdini would struggle to undo the damage done.
The Global Domino Effect
While tech giants boast about their encryption prowess, this breach exposes the sobering chasm between theory and practice. The ramifications extend far beyond social media—credential stuffing attacks, account takeovers, and waves of phishing schemes are now inevitable, and even corporate espionage gets a seat at the table.
This isn’t a haul for mere script kiddies; it’s a digital goldmine with the power to shake economies and upend trust in the very platforms people lean on daily.
Recent History: An Endless Stream of Breaches
This event joins a growing catalog of recent attacks. Utilities, like Nova Scotia Power, and education platforms, such as PowerSchool, have already experienced breaches with far-reaching consequences. The modern threat landscape is a tangled web where private and public sectors alike find themselves on the front lines.
The lines between personal and institutional risk blur more with every incident—making sophisticated, multi-pronged cybersecurity not just advisable but essential.
Who Pays? Users, Lawmakers, and Platform Providers
Ethics, Regulation, and the Involuntary Victim
The malware-based nature of this breach highlights regulatory and ethical grey zones. Most victims are oblivious that their devices have become unwitting data fountains. Meanwhile, companies face mounting scrutiny to secure APIs and police third-party apps, while lawmakers scramble to catch up.
Jurisdictional gaps offer shelter to cybercriminals, and even frameworks like GDPR strain to keep pace with ever-more-sophisticated attacks. Cybersecurity is no longer a back-room IT issue—it’s a frontline geopolitical battleground.
Digital Russian Roulette: Where Does It End?
The sheer scale of this breach is a jolt—a pointed cue that treating cybersecurity as an afterthought is an existential risk. The irony? Despite wall-to-wall warnings, millions of credentials still spill onto the internet like digital confetti. Watchdogs are left chasing shadows, and ordinary users make desperate password changes, hoping they’re not fixing the barn door after the horse has already bolted.
As AI-powered adversaries loom and credential-based attacks escalate, the question remains: Will we upskill toddlers as digital watchdogs, or wait for the next catastrophe to force real change?