Credential Heist: How 184M Logins Leaked Online
The Database That Should Not Exist
Imagine waking up to find your private credentials tossed into a digital bargain bin—except there are 184 million others just like you. This is no hypothetical: cybersecurity researcher Jeremiah Fowler recently uncovered an unprotected database spilling over with sensitive logins from the likes of Apple, Google, Facebook, and more.
The gravity of this breach isn’t just in its scale, but in its predictability. With no encryption, no password protection, and a recipe familiar to every cybercriminal, the incident exposes a disturbing glimpse into the state of global cybersecurity.
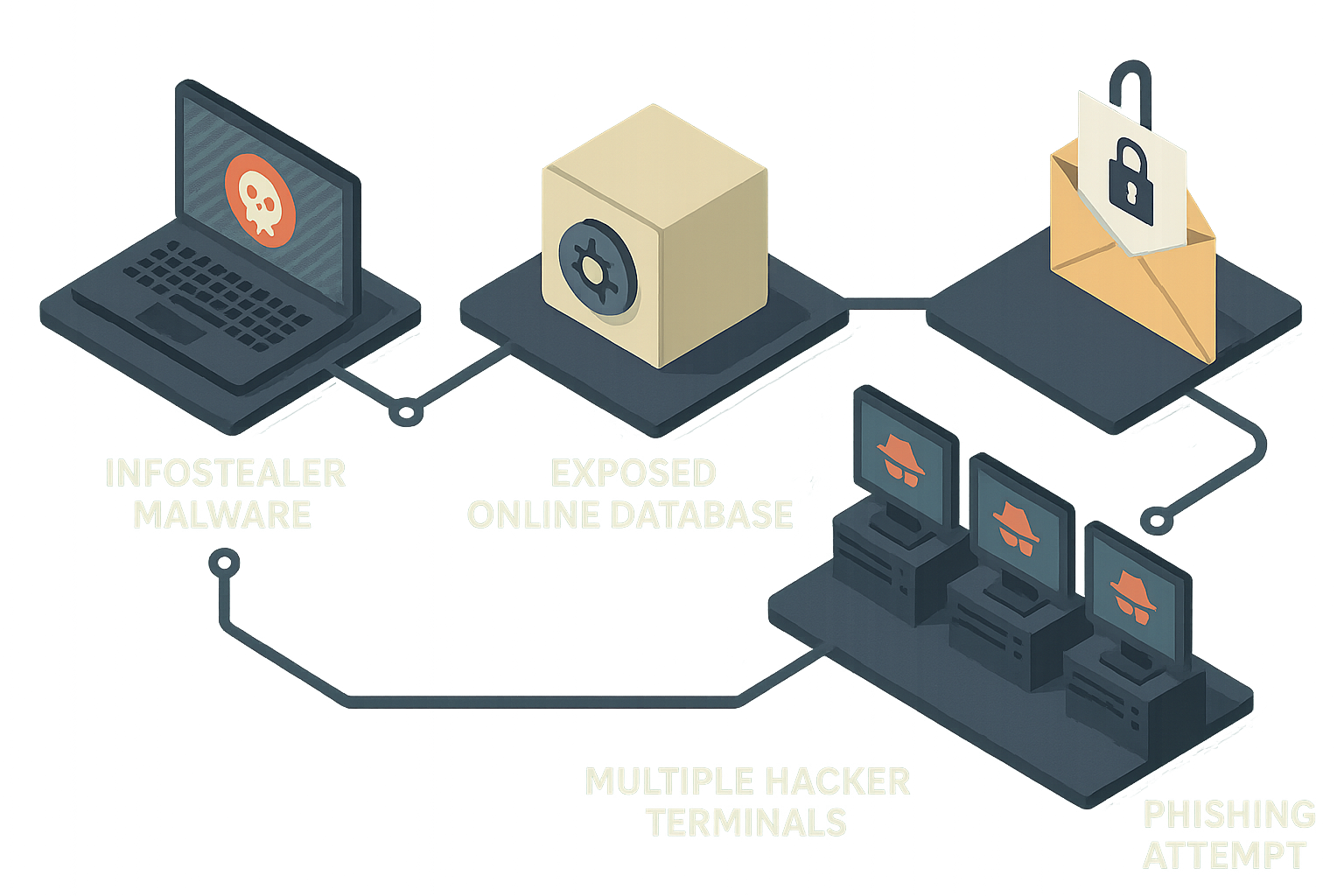
The Anatomy of a Catastrophe
Sitting Ducks: How Infostealers Feed the Black Market
The breached database was a hacker’s buffet—no security, no barriers, just millions of credentials, including those from major tech giants and .gov email addresses. Infostealer malware likely hoovered up this data from compromised systems, a process so routine it’s almost banal in the cybercrime world.
Despite the continuous drumbeat of warnings, many organizations still fail to implement basic security controls: encryption, two-factor authentication, or even strong passwords. Shockingly, in 2025, this is still the norm.
The Domino Effect: Why the Breach Matters
From Personal Hassle to National Risk
The consequences go far beyond a few compromised social accounts. Credential stuffing attacks, corporate espionage, and phishing schemes are all but guaranteed to spike. Even more alarming, the presence of government email addresses ramps up the stakes to a national security level, spanning countries from the US to Canada and Australia.
This isn’t just a personal or corporate failure—it’s a wake-up call for entire sectors and governments. Cybersecurity has evolved into a high-stakes geopolitical game, pitting not just companies but entire nations against a new breed of adversary.
When Regulation Is Just a Paper Shield
GDPR, CCPA, and their regulatory brethren all look mighty impressive on paper. Yet, this breach exposes a chasm between policy and practice. Without robust, enforced technical standards, even the best laws can’t hold back the tide of carelessness.
The Ethics (or Lack Thereof) of Data Stewardship
Let’s not forget the elephant in the server room: ethical responsibility. Tech giants and data handlers continue to sidestep meaningful safeguards, content to roll the dice with users’ digital lives. Stricter penalties and true accountability are long overdue—and the clock is ticking.
Time to Fly Under the Radar
The era of digital innocence is officially over. This breach is more than a PR disaster; it’s a sobering reminder of what’s at stake. Users need to adopt stronger digital habits, and everyone—from startups to global conglomerates—must take cybersecurity off autopilot.
Or perhaps, until the day quantum encryption for our thoughts arrives, we’re all just one step away from being the next open book in a criminal’s library.