Cloud Breaches: AT&T, Data Leaks, and Security Reckonings
The Myth of Cloud Invincibility
Cloud storage promised us the digital equivalent of Fort Knox, but recent events suggest it’s more like a glass house with a “Do Not Throw Stones” sign. The latest breach involving AT&T customer records isn’t just a headline—it’s a full-blown alarm bell for anyone storing sensitive data off-premises.
With hackers leaking nearly 88 million customer records, including over 44 million decrypted Social Security Numbers, cybersecurity’s perennial weaknesses have been exposed in dramatic fashion. Let’s dissect what went wrong—and, more importantly, what comes next.
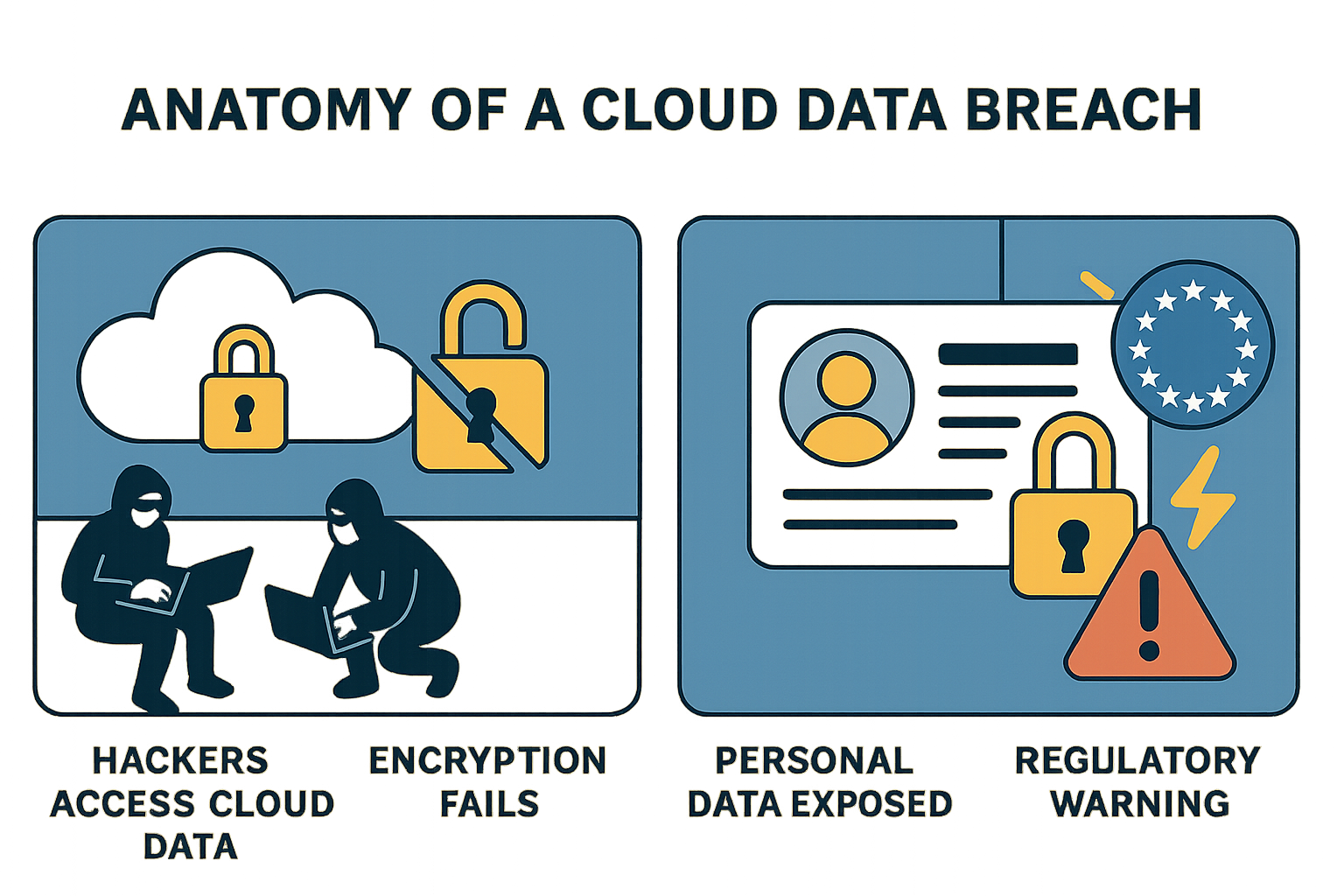
Cracking the Cloud: How AT&T Became a Cautionary Tale
The breach, first surfacing on a Russian cybercrime forum, was no ordinary slip. The ShinyHunters group claims responsibility, allegedly exploiting vulnerabilities in the Snowflake cloud data platform. The aftermath? Full names, dates of birth, phone numbers, addresses, and—yes— Social Security Numbers in convenient, human-readable text. It’s the equivalent of leaving the keys in the front door…and a welcome mat out front.
Encryption: Security Blanket or Tissue Paper?
The true horror of this breach isn’t just how much data was accessed, but how easily critical fields like SSNs were decrypted. Once trumpeted as the gold standard of protection, encryption here proved to be less of a bank vault, and more of a ziplock bag.
This is a sign: even robust encryption strategies are only as good as their implementation and key management. When threats know where and how to look, yesterday’s secrets become today’s headlines.
The Chilling Trend: Why Cloud Attacks Are Escalating
The Ransomware Boom
The AT&T leak is symptomatic of a broader pandemic. Ransomware attacks shot up 46% in the first quarter of 2025, targeting everything from cloud gateways to operational technology systems. As the Honeywell Cyber Threat Report notes, we’re now facing attacks that don’t just aim for data—they’re looking to kneecap the operations of major industries.
Human Error and Design Flaws: The Hidden Gremlins
While marketing departments peddle cloud solutions as the answer to all your prayers, the reality is less celestial. Flaws in system design, combined with classic mistakes (think: password123), are helping attackers waltz right in. Sophisticated hackers love nothing more than an innocent misconfiguration.
Regulation, Response, and the Long Road Ahead
Regulatory Shrugs and Customer Anxiety
AT&T’s official response is, let’s say, cautious—hinting that the leaked data may just be a remix of old breaches. For customers, that does about as much to calm nerves as free credit monitoring after a heist. Fundamentally, the breach spotlights the gap between regulatory requirements and real-world implementation of security controls.
The Call to Action: Security as Daily Practice
This latest incident is yet another reminder: cybersecurity can’t be an afterthought. Advanced measures—multi-factor authentication, regular patching, aggressive monitoring—aren’t “nice-to-haves.” They’re table stakes.
With AI-powered tools making stalking and tracking easier than ever, defending personal data is quickly becoming everyone’s problem. The Wild West of digital information needs more than tumbleweeds and wishful thinking—it needs sustained vigilance and investment.
The (Uncomfortable) Future: Trust Issues in the Cloud
Perhaps security tattoos aren’t practical just yet, but the AT&T breach is a warning shot for anyone assuming safety in numbers means safety at all. As cloud reliance grows, so does the potential for disaster. Companies and individuals need to approach the cloud with open eyes, sharp skepticism, and, ideally, a good deal of healthy paranoia.