SAP NetWeaver Hacks: The State-Sponsored Cyber Thriller
Welcome to the High-Stakes World of Cyber-Espionage
If you thought state-sponsored cyber-espionage was reserved for popcorn-fueled blockbusters, think again. Real-world attackers are scripting sophisticated breaches with alarming regularity, and their latest favorite target is SAP NetWeaver Visual Composer—a linchpin in critical infrastructures worldwide.
So, forget the Hollywood tropes. This digital siege is global, its fallout potentially catastrophic, and the drama is unfolding in your own backyard.
The Bone-Chilling CVE-2025-31324 Flaw
How a Simple Upload Turns Into Pandemonium
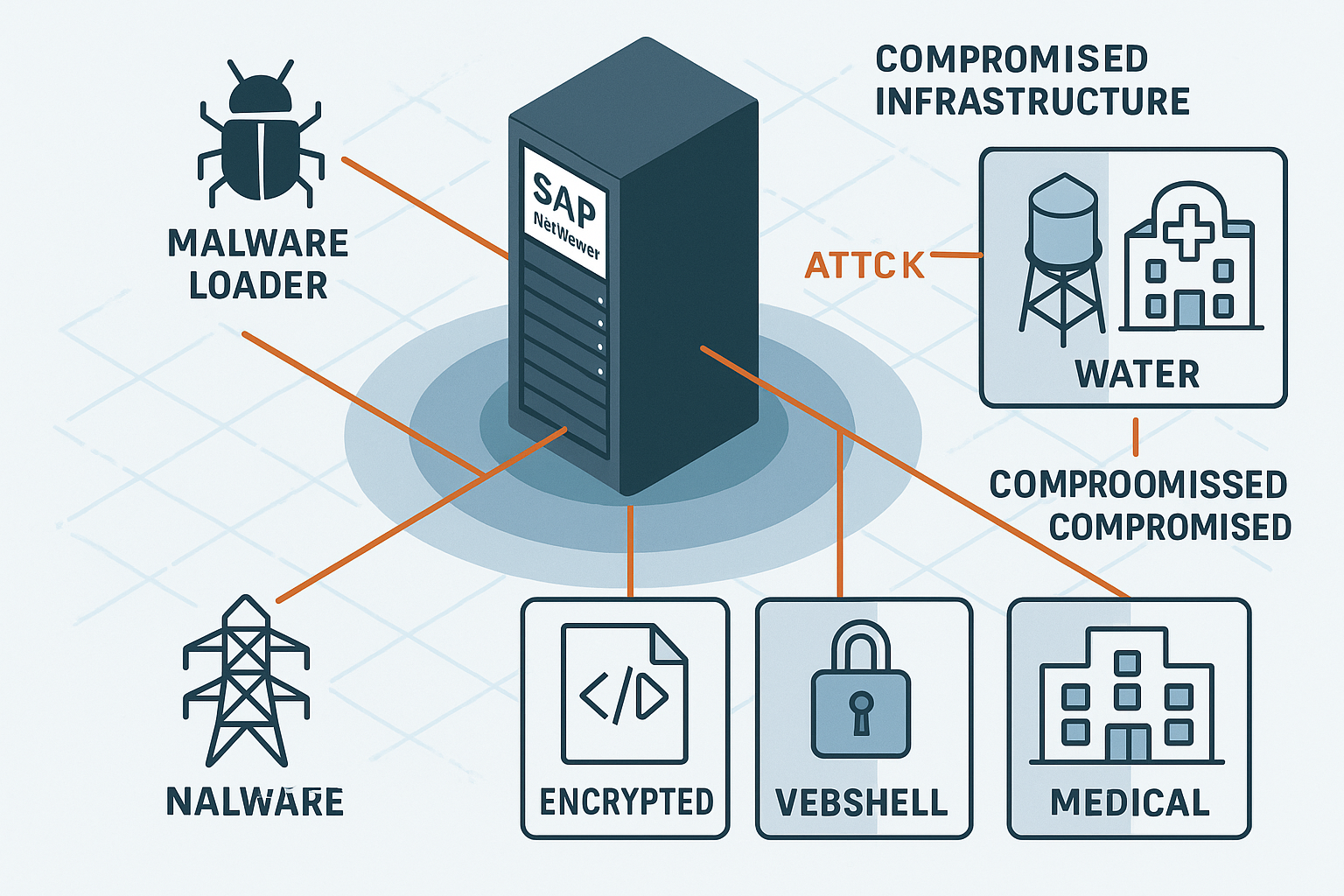
At the eye of this cyberstorm sits CVE-2025-31324, a critical unauthenticated file upload vulnerability. Scoring a hair-raising 9.8 on the CVSS scale, it allows attackers to waltz uninvited into enterprise networks. The worst part? These networks often route directly to operational technologies—think cloud identity platforms and VMware ESXi—laying out a welcome mat for multiply destructive consequences.
Chinese state-backed threat groups (UNC5221, UNC5174, and CL-STA-0048, to name a few) have elevated exploitation to an art form. They leverage encrypted webshells and customized malware like KrustyLoader and SNOWLIGHT to implant advanced persistent threats such as Sliver and VShell. The end goal: long-term espionage, quiet data heists, and the lingering threat of sabotage, especially in sectors like energy, water, and medical manufacturing.
Why This Isn’t Just Another Headline
This drama goes beyond national security and economic soundbites. It exposes a systemic ailment: critical enterprise software is riddled with weak segmentation and outdated cybersecurity hygiene. With SAP NetWeaver at the core of mission-critical services, one small breach can ripple across entire ecosystems.
The attackers’ toolkit—complete with in-memory malware and DNS beaconing—renders traditional defenses nearly moot, shifting the cat-and-mouse game to deep inside network perimeters where only the savviest hunters dare operate.
The Great Hybrid Heist: Perimeterless Threats
Hybrid Clouds: The Double-Edged Sword
Exploits like these are no outliers. They mark an escalating trend across hybrid IT environments, where cloud and on-prem worlds collide and expand the digital attack surface. Threat groups such as BlackBasta and Scattered Spider demonstrate chillingly effective lateral movement, seamlessly pivoting between platforms once inside. Meanwhile, the rise of ransomware-as-a-service models turns sophisticated crime into an all-access event.
Regulations, Reality, and the Achilles’ Heel
As governments and industry scramble to catch up, the regulatory merry-go-round is spinning faster. Fresh mandates push for stricter patching, sharper vendor oversight, and improved supply chain hygiene—hard lessons as third-party breaches spill sensitive data and drain millions each week. A vendor mishap is a front-door key for attackers, and everyone’s learning that the hard way.
A Perfect Storm for the Digital Age
Why Traditional Defenses Aren’t Enough
The confluence of cyber espionage, critical infrastructure, and hybrid environments is a storm no one wants to chase. With encrypted tunnels, reverse shells, and stealthy loaders, attackers sidestep even robust segmentation and perimeter controls. The SAP NetWeaver exploit isn’t just an alert for those directly hit—it’s a blaring wake-up call for every enterprise betting the farm on static defenses.
The Path Forward: Vigilance Over Checklists
Patching fast, segmenting networks, tightening credentials, and leveling up threat analytics—all necessary, yet not quite sufficient. The true shift must happen in organizational mindset: from reactive compliance to proactive, adaptive resilience. Otherwise, the list of ‘trusted’ platforms turned liabilities will just keep growing.
There’s Shakespearean irony here. Tools built to boost enterprise efficiency have become the very doorway for digital adversaries blending spy-novel patience with high-tech stealth. This isn’t sci-fi dystopia—it’s the day-to-day reality for those defending digital kingdoms in a world where conflict is increasingly silent but devastatingly real.
Cybersecurity Culture Shock: Prep the Toddlers?
As you digest the latest chapter in this cyber epic, maybe it’s time to ask: should cybersecurity and AI ethics be preschool curricula staples, or do we wait until daily breaches feel as routine as spam?
For deep dives on attacker tactics and SAP exploitation, see the latest analyses at Cybersecurity Trend Reports and expert threat intelligence updates.