The Utterly Unencrypted: Anatomy of a Password Apocalypse
When Cybersecurity Complacency Becomes Catastrophe
If you thought leaving your front door wide open was risky, imagine doing it online with 184 million keys labeled with your address. That’s precisely the digital disaster the “World Host Group” has unleashed, leaving passwords, emails, and addresses—tied to tech giants and sensitive sectors—exposed for all to see.
Yes, you read that right: plaintext passwords, out in the wild, inviting hackers to a virtual smash-and-grab. As the cybersecurity world reels, the rest of us are left pondering: is our digital infrastructure fundamentally broken?
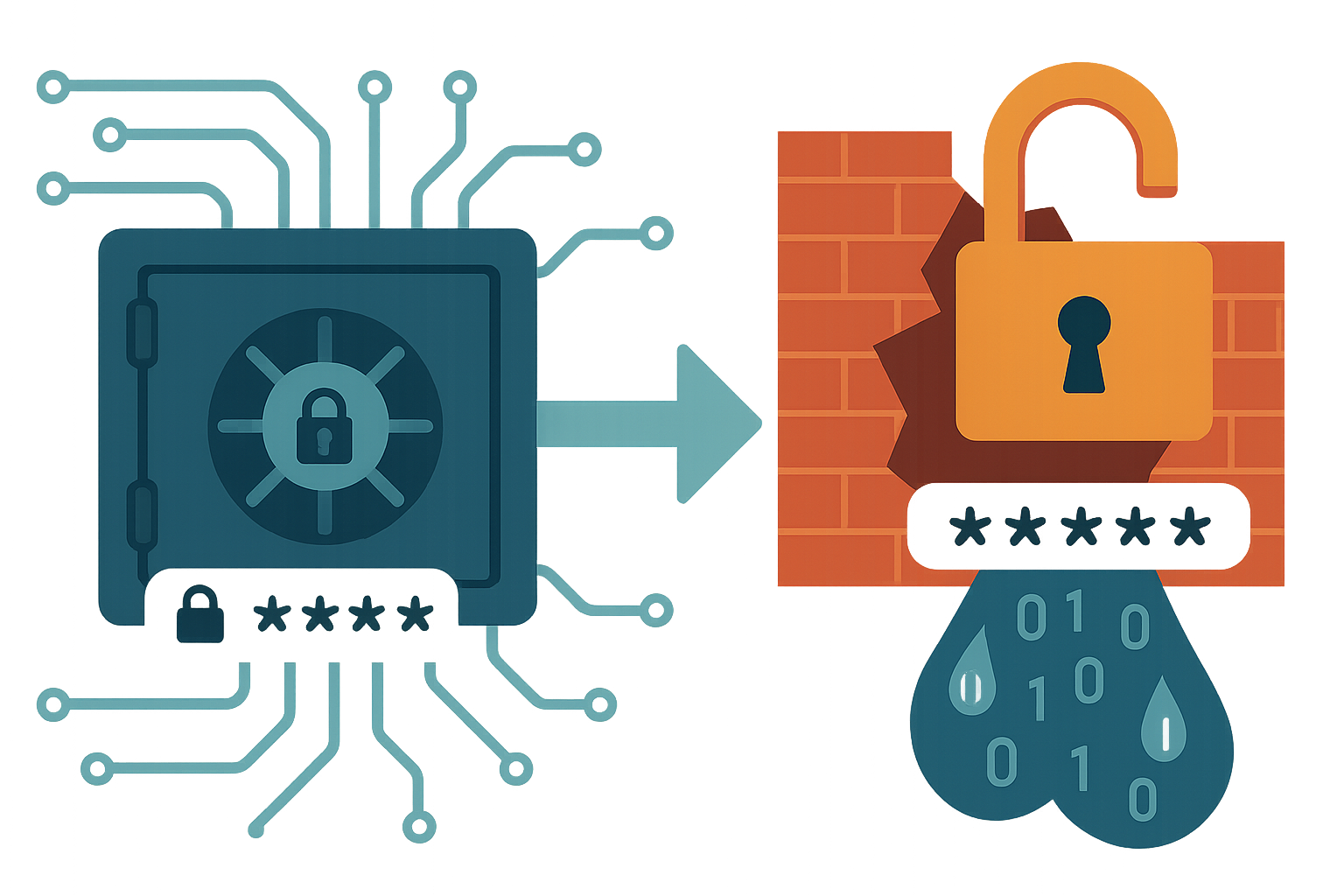
A Breach by Any Other Name: The World Host Group Debacle
Jeremiah Fowler, a vigilant cybersecurity researcher, stumbled upon a database bonanza that should never have existed: not some obscure service, but a trove linking major platforms like Google, Apple, Microsoft, Facebook, and even Snapchat. The problem? This vast quantity of credentials wasn’t encrypted, masked, or even mildly obfuscated. It was as if someone took their safe, propped it open in Times Square, and pinned a map to your valuables.
Plaintext Purgatory: Basic Security 101
Storing passwords in plain text is a sin so egregious, it feels medieval in an industry obsessed with zero trust and encrypted everything. There was no need for hacking prowess here—just a curious mouse click and the doors swung open. Though the hosting provider yanked the plug after the alarm was raised, the owner’s identity remains as foggy as the logic that led to such blunders.
Bigger Than One Breach: A Symptom of Systemic Failure
While this breach is headline-worthy, its scale signifies a deeper rot. The fallout extends well beyond social media: compromised records span banking, medical services, and even government infrastructure. This isn’t merely bad luck—it’s a warning siren about endemic shortcomings in data stewardship entrusted to third parties.
If your data is floating unprotected, it no longer matters how many two-factor-authentication codes you juggle; negligence somewhere upstream can still leave you exposed.
Whodunit? The Ethics and the Accountability Maze
The obligatory finger-pointing has begun: is it the hosting company’s fault? The anonymous database owner’s? Or perhaps the users, for recycling passwords? The reality is, all parties bear a slice of responsibility, but the greatest burden falls on those who failed to encrypt and defend the data in the first place.
In today’s digital ecosystem, “oops” doesn’t cut it. We need regulatory backbones—something more robust than public shaming and after-the-fact notifications via tools like “Have I Been Pwned?”
The Patchwork Defense: Why Updates Aren’t Enough
Ironically, all this unfolds while giants like Google scramble to plug holes in other parts of the ship—rolling out security patches to patch vulnerabilities before they’re weaponized. But, as this breach proves, defensive development at the software level can be rendered moot if basic custodianship isn’t respected by every player in the chain.
The lesson? For all the high-profile exploits and zero-days, old-fashioned carelessness remains a top adversary.
Locking Digital Doors: Toward a More Secure Tomorrow
This password apocalypse will (hopefully) serve as motivation for both users and companies to treat digital ID with the same paranoia reserved for their physical valuables. Encryption isn’t just a buzzword—it’s the bedrock of trust on which our online lives are built.
As the regulatory landscape slowly evolves, let’s hope complacency becomes the exception, not the norm. Until then, the burden of vigilance falls on all of us: Change those passwords regularly, scrutinize your digital footprint, and never, ever assume security is someone else’s problem.