Third-Party Cyber Attacks: The Modern Supply Chain Nightmare
A Chain is Only as Strong as its Riskiest Vendor
If recent headlines have you feeling paranoid about your partners, congratulations—you’re paying attention. The latest breaches at organizations as varied as ConnectWise, Victoria’s Secret, and Adidas have all stemmed from a familiar, quietly horrifying source: third-party vulnerabilities.
If you thought your digital fortress was safe, let this wave of attacks serve as a wake-up call. The truth? Your cybersecurity is now judged not by your defenses, but by the least diligent vendor on your roster.
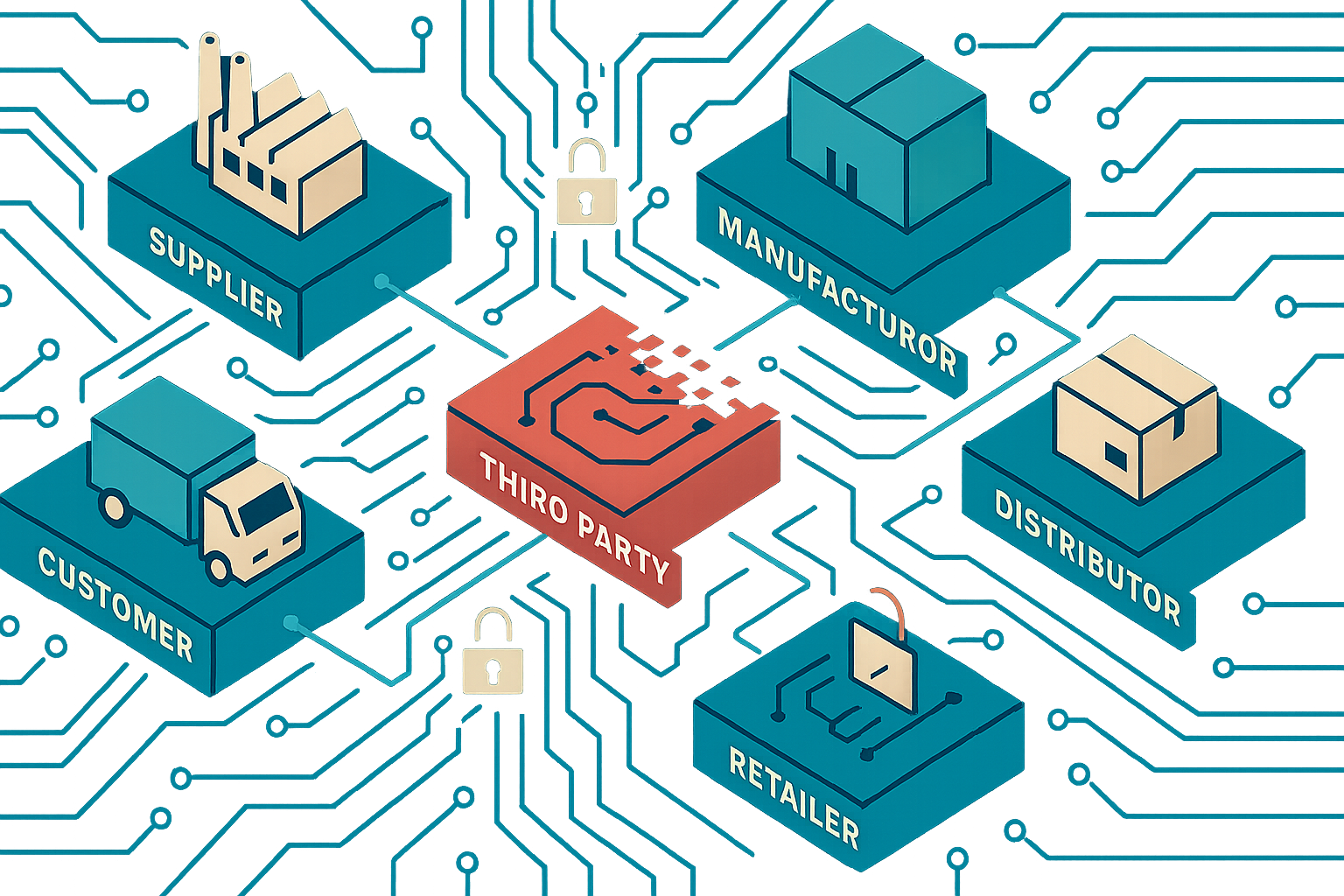
The Cascade of Compromise
Vulnerabilities with a Domino Effect
The data breach at Adidas—triggered not by a hacker’s wizardry, but by a vulnerable customer service provider—illustrates the domino effect of third-party attacks. When outside systems are compromised, customer data and trust fall in quick succession. MathWorks, creators of Matlab and Simulink, learned this the hard way when an unknown attacker leveraged external vulnerabilities, culminating in a ransomware event that brought both their customer-facing and internal systems to a screeching halt.
This isn’t random bad luck. A 34% year-over-year jump in exploited vulnerabilities, as cited in the 2025 Data Breach Investigations Report by Verizon, underscores a broader trend: cybercriminals have realized it’s far more efficient to squeeze through the neighbor’s window than bash down your front door.
The Exploitation Economy
Why Ransomware Gangs Love Your Vendors
Enter DragonForce, a ransomware crew making headlines for targeting managed service providers through third-party tools like SimpleHelp. By compromising one tool, they can inject ransomware into multiple downstream customers—a nefarious trick worthy of a standing ovation (from the wrong audience, obviously).
This strategy preys on the uncomfortable reality that just 54% of edge device vulnerabilities get fully patched, leaving plenty of digital backdoors unlocked for attackers with a knack for supply chain infiltration.
Regulatory Reckonings and Ethical Quandaries
Who’s Really Responsible?
Gone are the days when companies could feign ignorance of their supply chain’s security posture. Regulators are tightening the screws, demanding accountability from organizations for the security practices of third, fourth, and even fifth parties. If you’re thinking this seems unfair, you’re only half right—though it’s not just about playing defense; it’s about maintaining the trust of customers, stakeholders, and, yes, the regulators ready to fine you into oblivion.
Ethically, the issue is murky: Should companies shoulder full responsibility for their vendors’ lapses? Maybe not, but they certainly can’t wash their hands of it, either. Vetting, auditing, and enforcing standards have become table stakes, not optional flourishes.
Where Do We Go From Here?
If the digital ecosystem is only as secure as its most careless participant, organizations now face an uncomfortable choice: treat third-party cybersecurity like a core business function, or wait for a headline-bearing breach. The interconnectedness of our online world means every partnership is a potential liability—and every unpatched portal, an invitation for disaster.
Proactivity is the order of the day. Mandating cybersecurity audits for vendors isn’t just prudent; it’s becoming standard practice. In this ongoing cyber arms race, trust must be earned, verified, and—where possible—encrypted.