Unsecured Databases: The Silent Cybersecurity Catastrophe
When Passwords Leak and Identities Fray
Just when you thought your digital persona was safely tucked away behind a password or two, another breach comes along to prove otherwise. The most recent database debacle—exposing login credentials of 184 million users—follows the grand tradition of cyber calamities like the RockYou2024 mega-leak.
For anyone logging in via Apple, Google, or Meta, the risk is more than theoretical. This isn’t just a story about data exposure; it’s a cautionary tale about convenience, complacency, and the perpetual domino effect of bad password practices.
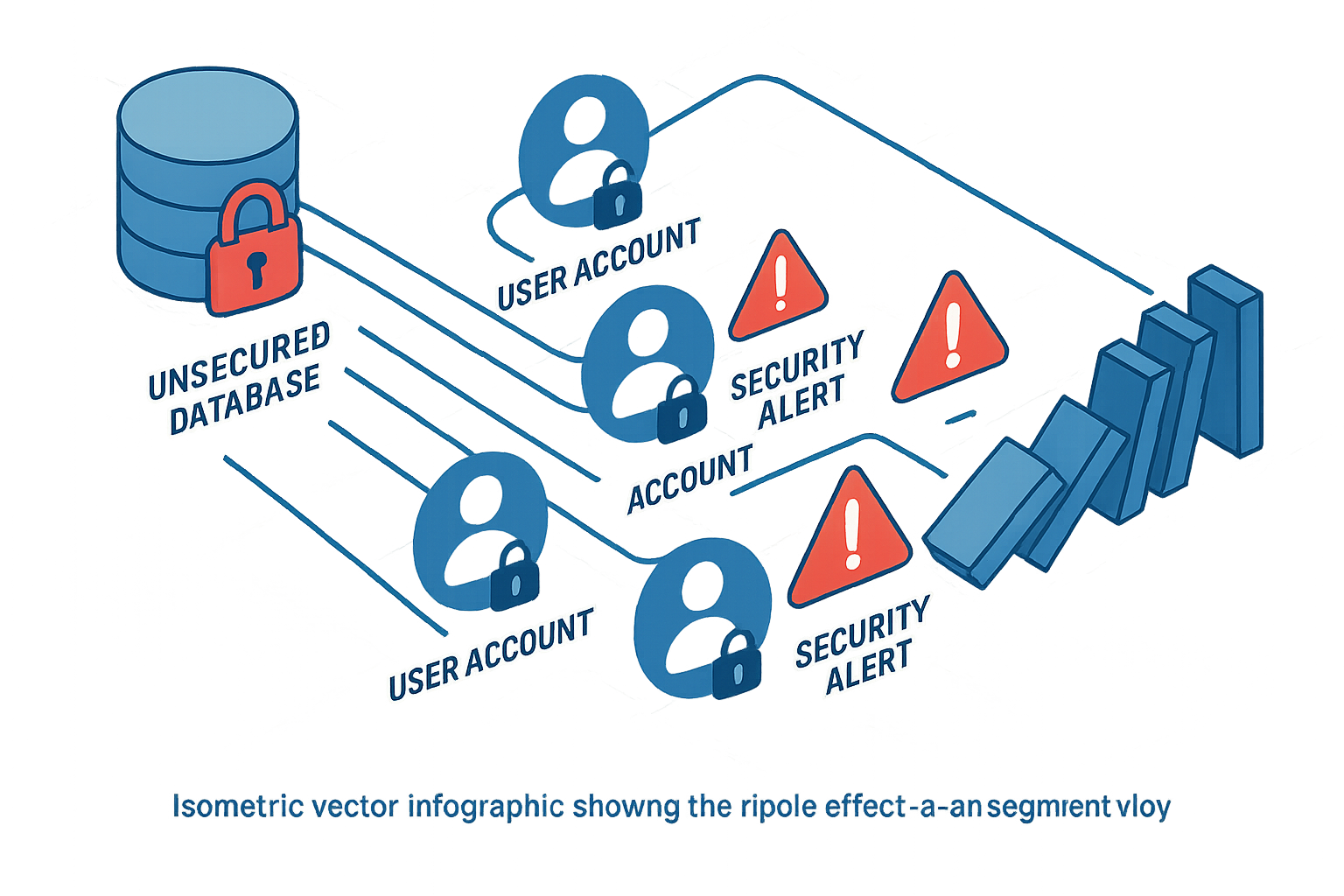
The Scope of the Database Meltdown
Let’s get specific: an unsecured third-party database has spilled the digital keys to a kingdom of accounts, ranging from email inboxes to streaming services. With Apple, Google, and Meta all inadvertently involved, no one’s entertainment or communication platforms are immune.
The Numbers Game
If 184 million seems colossal, remember it sits next to the infamous RockYou2024 leak’s 19 billion exposed passwords—a number so large, even your password manager is sweating.
The Endless Loop of Bad Passwords
Most breaches don’t require black-hooded hackers—just reused passwords and exposed credentials. Every time a user recycles a pet’s name for another login, they open the door to credential stuffing attacks that can cascade across platforms.
Experts recommend changing passwords for critical accounts and enabling two-factor authentication (2FA). It may feel like digital Pilates, but it’s the best way to stretch your security muscles.
Third-Party Pitfalls: Companies Beware
It’s not just lazy users at fault. This breach underscores the peril of outsourcing and unchecked third-party access. Companies must treat every database like the crown jewels and adopt rigorous security standards—not just tick compliance checklists.
The Geopolitical Undercurrents of Cybercrime
Enter the international intrigue: malicious groups like “Laundry Bear” and “Void Blizzard” aren’t operating from dimly lit basements, but as cogs in nation-state machines with strategic agendas. Password spraying—where hackers systematically guess common credentials—remains a favorite tactic, made even easier by leaks like this.
Worse yet, the democratization of hacking tools means you don’t have to be a genius in a hoodie; you just need internet access and questionable morals.
Finding a Path Forward
The modern security checklist is simple—unique passwords, 2FA, and offline backups—but the challenge is psychological, not technological. Will companies prioritize robust security over racing to market? Or will we persist in rewarding speed and innovation at the expense of our digital identities?
This latest breach is a reminder that, in cybersecurity, the status quo is less “lock and key,” more “hope and pray.” Perhaps it’s time for a culture shift—where safety is as celebrated as speed, and vigilance is valued over convenience.